External or internal cyberthreats to government and public sector data?

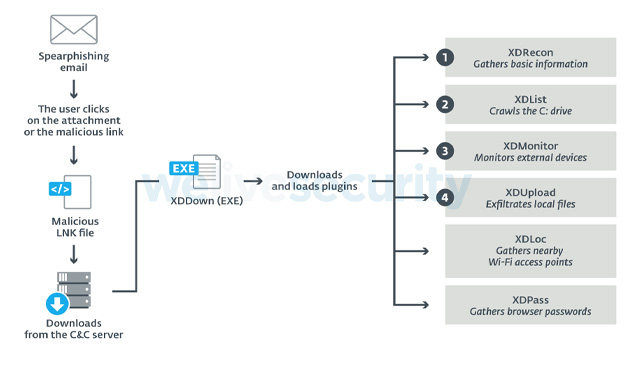
Last October, ESET researchers uncovered an Advanced Persistent Threat group that has been stealing sensitive documents from several governments in Eastern Europe and the Balkans since 2011. Named XDSpy by ESET, the APT group has gone largely undetected for nine years, during which it has compromised many government agencies and private companies, using spear phishing emails in order to compromise their targets.
The emails displayed a slight variance, as some contained an attachment, while others contained a link to a malicious file. Before that, in August, several Canadian government services were disabled following a series of cyberattacks. On 15 August, the Treasury Board Secretariat announced that approximately 11,000 online government services accounts, originating from the Government of Canada Key service and Canada Revenue Agency accounts, had been victims of hacking attempts.
A year before that over 752,000 birth certificate applications have been exposed online by an unnamed company that enables people to obtain copies of birth and death records from state governments in the United States. Over a 12-month span between June 2018 and May 2019, a total of 2.3 billion files were discovered exposed online due to misconfigured or non-secured file storage and sharing technologies.
These are just some examples of various threats to state organisations and infrastructure that we repeatedly read about. Some are external, like hackers, sometimes state-backed, others are organised crime and some originate from within, either through malicious activity or just negligence or bad design. Some headlines from Ireland from a while ago included: “Personal data of 380,000 welfare recipients stolen” (The Irish Times, 2008), “75,000 customers’ bank details on stolen Bord Gáis laptop” (Siliconrepublic, 2009), “Lost Phoenix Ireland data tape had details of 62,000 customers” (Databreaches, 2011), but that was in the pre-GDPR era, right, when things weren’t regulated yet? Well, just over a month ago, we could read about “Thousands have highly personal details exposed in Covid-19 vaccine data breach” (Extra, 2021), and a year earlier we could read that “Ireland had fourth most data breach notifications in the EU last year” (Extra, 2020).
So what is it with data security and why is it such a headache? Well, unlike in the pre-digital era, when stealing a database would entail a truckload of paper having to be hauled around, today huge databases with thousands of entries can be attached to an email or put on a flash drive. The key questions are therefore how access is regulated and how secure the storage is. Who can access the data and what can they do with it, can it be accessed by unauthorised people and can they copy or manipulate it in any way. In 2016, the UK’s communications regulator Ofcom was investigating the biggest data breach in its history. The incident was caused internally – a former employee had been surreptitiously gathering data over a six-year period. The breach only came to light after the individual offered the information to his new employer, a major TV broadcaster.
Insider threats can be both intentional and unintentional. They are influenced by technical, behavioural, and organisational issues, meaning that organisations need to consider solutions that address each of these key areas of weakness to ensure they have responses to most scenarios. Three years ago, a survey for Accenture revealed that almost one in five (18 per cent) employees in the healthcare industry in the United States and Canada said that they would be willing to give access to confidential medical data about patients to an unauthorized outsider for financial gain. They would expect no more than $500 to $1,000 for their login credentials or for deliberately installing tracking software or downloading the data to a portable drive. In addition, this way of compromising patient data is not a purely hypothetical phenomenon. Roughly one in four (24 per cent) respondents said that they were actually aware of a co-worker who had made a profit by providing a third party with access to such information.
All this reveals that whether initiated externally, or coming from within the organisation, the “human factor” is the weakest link of data protection. In fact, a 2015 paper by Nuix, reported that the overwhelming majority of respondents (93 per cent) consider “human behaviour” to be the number one threat to their security. So what can be done about it?
1. Know about the threats
The first step in preventing cyberthreats is knowing about them. Following general cybersecurity news, browsing through the headlines of IT topics, anything is good just to get a feel of what sorts of threats are currently trending and help recognise them when encountered and increase the chance of avoiding them.
2. Regulation and access control
Security clearance for access to data should be strictly regulated and enforced in every organisation, so that unauthorised people do not even gain access to sensitive data, while authorised ones are accountable and tracked for any transfer, removal or manipulation of data.
3. Employee education
Employees need to be regularly educated and briefed on any current external types of threats, particularly ones that initiate the breach through social engineering, which takes advantage of the employees themselves, by asking them to open a file attachment or click on a compromised link in order to gain access.
4. Encryption
Well encrypted data is pretty useless to any attackers, even when successfully exfiltrated from an organisation as current encryption tools are practically impossible to decrypt by unauthorised prying eyes. That is why GDPR legislation mentions encryption as one of the recommended tools, although not mandatory, in mitigation of potential damage caused by data breaches.
5. Secure backup and storage
Secure backup of sensitive data is key to long-term data breach prevention. Whether on-site or cloud storage is used, strict protocols on content, control and accessibility, as well as accountability of the storage provider need to be observed in order to ensure maximum data security and data loss prevention.
6. System Patching and Multi Factor Authentication
Administrators should also endeavour to ensure their systems are regularly updated to prevent exploitation of known vulnerabilities and employ Multi Factor Authentication as another valuable layer in the prevention of account hijacking.
Threats to cybersecurity of government and public sector institutions are therefore many and varied, can come from outside or inside and can cause various degrees of difficulties and disruptions. But overall, while countering them may appear very intimidating at first, mostly all can be avoided with proper planning and introduction of even some relatively simple measures. Security professionals have spent years coming up with optimal prevention measures, solutions and best practices for most threat scenarios, so the know-how and the hardware are there. With a bit of effort to put it all together, there is really no obstacle to properly benefit from and enjoy safer technology.
T: +353 53 914 6600
E: info@eset.ie
W: www.eset.ie






