Safeguarding government and citizen data


Against the backdrop of a rapidly evolving climate of technology and subsequent security breaches, Accenture’s Pat Power and Dan Sheils unpack the need for public service organisations to develop a proactive and holistic approach to counter the cybersecurity risk.
Governments around the world are working to meet citizens’ growing expectations for more and better digital public services. Across health, education, policing, revenue, postal and social services, digital technologies are fuelling incredible innovations, and changing the way governments interact with their citizens.
Yet the same technologies that enable better service delivery and enhance citizen experiences also contribute to cybersecurity risks. Whether originating from inside an organisation or from a threat actor on the other side of the world, cyber threats are real, are growing in number and complexity and, unfortunately are here to stay.
Every government department or agency operates with a unique mission – often with a constrained budget and limited resources. In the face of these realities, how can government effectively and efficiently safeguard their information systems and data?
Success lies not only in investing in the latest security technology, perimeter protection, or monitoring services – though these all have a role to play in a cybersecurity programme – but also in developing and implementing a practical, proactive approach to cybersecurity across the entire organisation. Public service organisations should assess the risks they face and build a flexible strategy to address. This will involve a blend of technical and governmental expertise essential to staying ahead of emerging risks.
Drivers of cyber insecurity
The 2017 WannaCry and Petya ransomware attacks clearly demonstrate the devastating impact that cyberattacks can have. Recent analysis suggests that public service organisations and key national infrastructure networks are a particularly desirable target for breaches and cyber-attacks. Indeed, 50 times more attacks were launched against government targets in the past year than any other industry. i
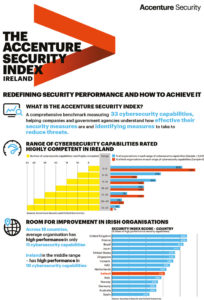
Though it is seen as a particularly desirable target, government is not alone in facing threats to data security and business continuity. In fact, a recent Accenture global survey of 2,000 security executives across industries – including respondents from Ireland – revealed that roughly one in three targeted breach attempts against their organisations succeed. Of the Irish respondents, more than half (52 per cent) admitted it can take “months” to detect successful breaches, while almost one-third (29 per cent) admitted it took “a year or longer”. Respondents also reported that internal security teams discover almost two-thirds (65 per cent) of effective breaches, with employees, law enforcement and “white hats” (that is, “ethical” hackers) identifying most of the breaches. ii
With many security breaches going undiscovered, all organisations should be concerned about the privacy and security of the data they hold. For governments, the threat of loss or manipulation of citizen data is now critical and one that requires immediate action.
Today’s hot list
Security breaches can come from numerous sources inside and outside an organisation, and threats are nothing if not diverse and dynamic. Just when an organisation believes it can successfully defend against one type of attack, another attack, technique or vector emerges. Though risks are always changing, here are some of today’s most pressing:
• Rise of ransomware: Attackers often send ‘phishing’ type emails to company and employee email lists. When the link within the message is clicked upon by the receiver, the computer is rendered unusable until a requested ransom is paid. Other ransomware attacks see government agencies receive a warning letter threatening to take down its network unless a ransom is paid (typically to be paid using Bitcoin or another crypto-currency). In 2016, a ransomware attack named ‘Locky’ targeted organisations around the world. Hospitals and medical institutions – with their life-and-death reliance on systems and data – were particularly impacted, causing much disruption to the administration of patient services. In 2017, the ‘WannaCry’ ransomware attack affected an estimated 200,000 organisations in 150 countries, locking-up the data of factories, hospitals, shops and schools across the world, and sending security companies scrambling to develop urgent fixes wherever possible.
• Internet of things (IOT) security: A growing number of ‘things’, from cameras to medical devices, are going online. Unfortunately, when it comes to internet of things (IoT) devices, security standards have often been an afterthought and are not required to meet any basic industry standards. Low levels of security can leave government owned and operated IoT devices vulnerable to security breaches, putting the data they hold and share at risk of theft or manipulation. As IoT devices become ubiquitous, there will be an increased risk of these devices being hacked and manipulated by third parties to cause ever-greater damage. This ‘bot’ technique was demonstrated in October 2016, when hackers attacked infrastructure provider Dyn, which serves as a switchboard for Internet traffic. Using malware to harness webcams, digital recorders and other common connected devices, the complex attack caused outages that started in the eastern part of the U.S. and spread across North America and on to Europe – striking many prominent businesses and websites. iii
• Cloud security: For many governments, moving systems and data to the cloud is helping increase IT agility and contain data storage costs. Yet, cloud computing must be undertaken with a careful eye towards security threats and risks. Citizens seem strongly aware of the potential benefits of new cloud technologies but also of the risks involved with cloud deployment. In a recent Citizen Survey undertaken by Accenture, three-quarters of respondents indicated that they are concerned about cybercrime, with half saying that their concern about cybercrime is limiting their use of online services, many of such services are hosted in the cloud. This high-level of citizen concern around the use of new technologies, and of becoming a victim of cyber-crime underscores the need for careful and disciplined security planning as part of every cloud implementation.
• Mobile threats: Smartphones have become a valuable channel for governments and service providers to engage citizens, and through which they deliver their services. However, security options remain limited when it comes to strong authentication and data encryption for most mobile devices. These relatively low security levels present a high-risk if a device is lost or stolen. Laptops and mobile devices are gateways to a user’s and organisation’s data – making them of high interest to hackers and threat actors. In recent times, we have seen an increase in malware and ransomware attacks deployed against mobile devices.
• Industrial internet of things/industrial control systems: Connected devices are gaining ground and introducing new risks in a host of industrial and infrastructure settings. As power plants, transportation systems, connected cities and other providers of state-run infrastructure adopt IoT-enabled capabilities, state-run organisations must ensure they have strong cybersecurity programs in place and the latest security tools deployed to ensure the continuity and security of critical national infrastructure. This lesson is well-illustrated by repeated hacking attacks against the power grid and military resources in Ukraine in December 2015, in what is widely viewed as the first major attack on a nation’s power supply.
The way forward
Safeguarding sensitive data against a backdrop of complex threats, the challenges of constrained budgets and the difficulties faced in finding top security expertise is on the minds of security professionals every day. How can government protect so much with resources that can never adequately address all risks and all threats? Accenture recommends a practical approach that balances cyber risks and digital rewards by embedding a rich security strategy at the core of all digital technology.
Here are five actions to take:
1. Build a cybersecurity strategy. A crisis response plan is not enough. Every government organisation also needs a proactive, holistic security strategy. The strategy needs to address not only the protection and security of data and technologies, but also the integration of these with other security measures, the creation of policies ‘fit for purpose’ in the digital age, and the training necessary for employees to be the first and last line of cyber defence.
2. Assess risk. Conduct a risk assessment to determine the areas of greatest vulnerability and potential consequences of an attack. To engineer effective defences, take a realistic and pragmatic view of the threat landscape and most likely scenarios. Conduct the assessment with both outside security experts and internal stakeholders.
3. Lead security efforts with intelligence, and rely on advanced analytics. Digital gates and guards used to be enough to protect networks and data but that is no longer the case. Effective protection now requires the use of advanced threat intelligence tools supported by advanced analytics technologies that can help identify and manage threats. For instance, employee behavioural analytics can use vast quantities of data from multiple sources to understand what normal network activity looks like and identify anomalous or questionable activities that arise in real-time.
4. Invest in cybersecurity talent. Across industries, cybersecurity expertise is in short supply, and many public service organisations find themselves lacking sufficient skills and competencies to thwart the array of digital threats that their organisations face. Public service leaders can overcome this skills shortage through allocating increased resources to attract and retain a strong in-house security team, while augmenting those in-house skills with third-party support through in-depth partnerships with industry and the academic community.
5. Increase stakeholder collaboration. ‘Inside jobs’ – that is, data theft, leakage or corruption by employees, whether intentionally or not—are among the most common sources of cybersecurity breaches. Thus, it is crucial to educate employees so everyone can play their part in protecting data. In particular, government employees need to understand the risks and security steps required of them when at work and when using mobile devices, social media or accessing citizen information. Alongside employee awareness and training, government agencies need to work with peer organisations, academia and the private sector to minimise risk. Such partnerships aren’t just about filling security roles or deploying new security tools – they will also ensure that government agencies are receiving innovative, ever-evolving insights into the security challenges of today, and those likely to arise in the future.
While every industry is facing challenges around keeping systems and data safe, government agencies face additional layers of risk and complexity. Securing the delivery of public services and citizen data requires an approach to security that can evolve and adapt based on an ever-changing threat landscape and that incorporates a distinct blend of government, technology and security expertise. In so doing, government organisations will be well-placed to address both the evolving cyber-threat landscape and take maximum advantage of the latest technologies to deliver citizen services safely and securely.
For more information, or to discuss your security requirements:
Pat Power, Head of Health & Public Service Consulting, Accenture Ireland
T: 01 646 2319
E: Patrick.power@accenture.com