Enterprise Mobile Management: the base of next-gen security


CWSI Chief Executive Ronan Murphy details the constant risk posed to individuals and organisations by mobile device usage and outlines the layered approach required to ensure a holistic defence against this.
Enterprise Mobility is a cross functional technology that impacts all areas of an organisation. It offers fantastic opportunities to improve or transform business processes, to improve productivity and drive down costs. However, organisations are struggling to leverage or even manage their mobile devices and projects. Joined up thinking is critical; organisations must look at the basics of delivering any change into an environment – people, process and technology. Focus on too much of any one of these and projects run a significant risk of failure.
On top of all of this complexity, there is the constant requirement to manage the risk of mobile to the organisation. Mobile devices are inherently risky as they are small, portable and easy to lose/have stolen, but at the same time can store large amounts of data.
As smart devices have become more prevalent in the enterprise and more integrated, they now offer a potentially far more attractive target than before. Smart devices can hold large amounts of personal and corporate data as well as offering an entry point for a potential attack on the organisation. We can see this clearly by the exponential increase in attacks on mobile devices over the last two years.
Are Enterprise Mobile Management tools sufficient?
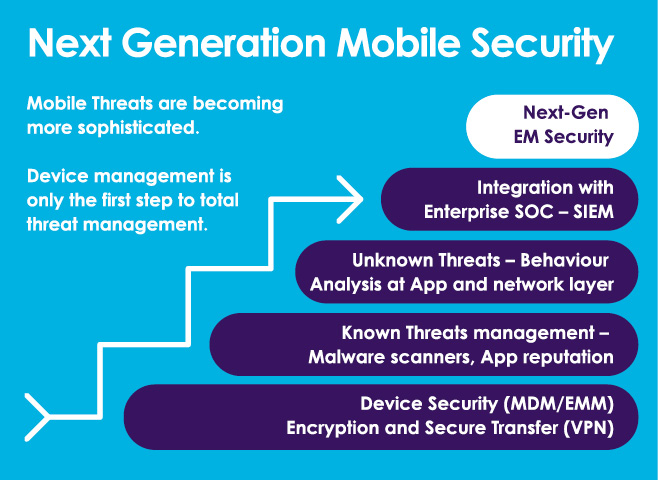
Device management controls are the first step in ensuring devices have basic security enabled. Most organisations at this point have some level of Enterprise Mobile Management (EMM) tool in place to manage their smart devices. These are implemented with varying degrees of success but at a minimum most have a passcode requirement, jailbreak or root detection, and encryption of some or all data on the device enabled. More mature deployments have implemented additional controls around data loss prevention by restricting corporate data from being shared to non-approved applications and possibly some device level restrictions, like preventing cut and paste, or screen grabs. Unfortunately, there can be resistance to this level of restriction as the user experience is impacted.
Are these types of controls described above enough? Unfortunately, the answer is probably no. Threat actors are now using sophisticated methods to attack users via their mobile devices at multiple layers, for example at the application and network layers using a variety of clever methods.
The most common seen in the market are:
- SMSiShing: hard to pronounce but easy to do! This is where attackers use phishing attacks via SMS to trick users into visiting a fake URL to harvest credentials or download an exploit. Typically presented as a message from a bank or service provider for example. In the enterprise, attackers are pivoting to use trusted contacts to send SMSs to request sensitive information or authorise payments. For example, an attacker can pose as the CFO and send an SMS to one of the accounting staff that supplier X has a new account number right before a payment is due. Of course the new account number is the attackers! It’s child’s play to fake the source number of an SMS, so this type of attack is both low effort and highly effective and is increasing exponentially.
- Application exploits: poorly written apps can expose credentials or provide a means to install an exploit. Some apps even come with malware hidden inside as hackers have managed to gain control of the development engines (XCode Ghost). Many applications are not centrally managed for patching which can expose vulnerabilities for long periods of time in older versions.
- Network attacks: ‘man in the middle’ attacks are probably the most common network attack, driven by users lack of awareness around unsecured Wi-Fi risks. It’s very easy to setup a fake Wi-Fi hotspot in a public space and trick users into using it. This can enable the attacker to proxy all of a user’s traffic and therefore monitor what websites they are browsing and any unencrypted data. Even encryption is not a complete defence as attackers can use techniques like SSL bumping, certificate spoofing and other advanced methods to read the encrypted data. They can also redirect the users traffic to URLs that will download exploits such as mRATS and keyloggers.
So how can organisations defend against all of these attacks?
As already mentioned EMM tools can help ensure the device is more secure and also use VPNs and containers to try and protect the data at rest and in transit however they do not provide constant threat analysis of applications installed or real time behavioural analysis of the network traffic.
An enterprise may whitelist and allow a particular app for access to corporate data however this is rarely targeted at a specific app version. Older versions of applications are more likely to have vulnerabilities and can present a risk as users rarely update.
Mobile users are by their nature, highly likely to use multiple Wi-Fi hotspots and therefore are very likely to be exposed to man in the middle attacks. EMM solutions cannot detect this type of attack as they have no visibility of the network traffic.
What’s needed is a layered defence approach. EMM is the foundation but requires other tools such as App Risk Assessment, Mobile Threat Prevention (MTP), and Secure Gateway type tools to provide a holistic view of the threats on mobile devices. The good news is that all of these tools exist and the market leaders all integrate seamlessly with EMM solutions to simplify provisioning and even enable automated remediation, for example, by removing all corporate data or even performing a device wipe.
This type of total mobile endpoint protection is becoming more and more critical in the light of both the increase in sophistication and volume of attacks but also due to the increased impact of data breaches on organisations from reputational damage and regulatory fines. The incoming EU General Data Protection (GDPR) has eye watering, potential fines of €20 million or 4 per cent of global turnover. But even these huge financial fines could be only part of the cost of a breach with the ability for affected data subjects to bring what amounts to a class action suit against the data controller and processor(s) involved.
Unfortunately, it is generally recognised that even with all of the layered defence described above there is still a chance that a breach could occur if an attacker was sufficiently skilled and motivated. In this case it’s critical to be able to understand how the breach happened and what the attackers did next, bearing in mind that the mobile device may have just been an entry point or even just a part of the reconnaissance stage of an attack. For effective data breach disclosure, it’s also critical to understand what was lost. In order to do this final part of what we call Next Generation EM Security, it is necessary to take all the information from the different tools and import it to the organisations SIEM. This is the logical next step to go from reactive basic device security to proactive automation for mobile endpoints and full audit and visibility of threats. In my opinion, no one vendor can do this yet, but it’s definitely possible to start tying these technologies together and integrating with security operations centres (SOC).
A recent Ponemon Institute study *, conducted on behalf of IBM Security and Arxan Technologies, surveyed 600 IT and IT security practitioners. Some of the interesting findings from this report were:
- 84% of respondents are very concerned about malware threats to their mobile applications.
- 75% of them say the use of mobile apps increase security risk significantly or very significantly.
- 63% of respondents are not confident (30%) or have no confidence (33%) their organizations know all of the mobile applications used by employees.
- A sobering 60%, or six out of 10 of the respondents, say their organization had been breached as the result of an insecure mobile application over the past 12 months.
The survey showed that less than 30% of mobile applications are tested for vulnerabilities and 44% confessed to taking no measures to protect their mobile environment.
*2017 Study on Mobile and IoT Application Security – Ponemon Institute
12 Sandyford Business Park, Sandyford, Dublin 18
Ireland: +353(0)1 293 2500
UK: +44(0) 2036 515 392
Web: www.cwsi.ie
email: info@cwsi.ie






